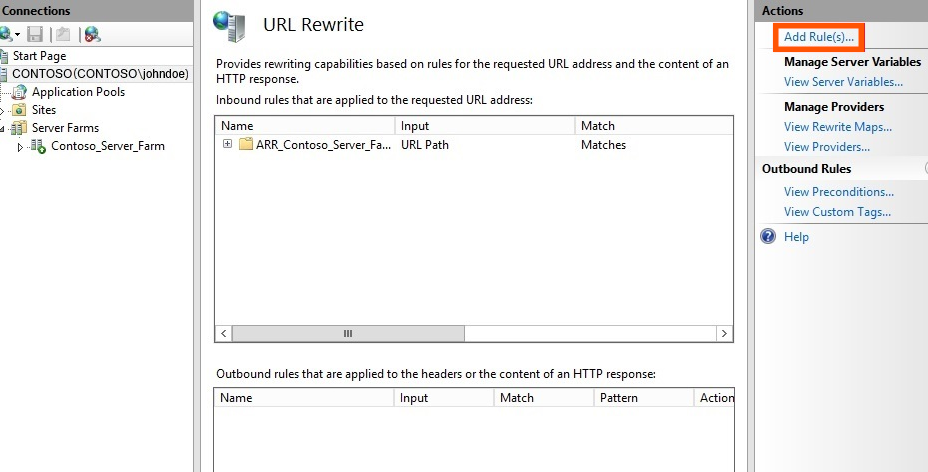
Have you ever encountered the peaks of unexplained access by examining data from Google Analytics for your website? Or have any significant increase in access to the site requires your attention with worsening performance? These sprouting number of spams in Google Analytics are rendering the reports useless for further analysis. An alarming trend of referral spam creeping in Google Analytics makes you more vigilant over the issue and how to fix it for better data insights. Due to flooding Referral Spams from social buttons and many other sources people are now combating the issue by applying filters to manage the useless data they are receiving.
Types of Referral Spam
With Due regards to Google Analytics, there are two flavors of Spam: Spammy Web Crawlers and Ghost referral traffic.
Ghost referral traffic being the majority of the spam with so-called ghost nature never access your website. It might seem wonder to you but since they never access your website, they do hamper the Google analytics that monitors your website traffic.The rocket science behind this is that they uses the measurement protocol, which allows the user to send data directly to Google Analytics. By using this, generally spammer generates a random code and leaves a “Fake VISIT” without even knowing who they are hitting.
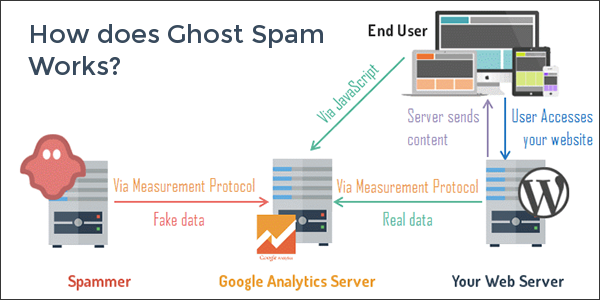
Crawlers in contrast to ghost referral traffic they do access your website and has a prominent presence in the Google search pages. These spams crawl your pages by ignoring the rules like robots.txt that are supposed to stop spiders from crawling specified pages. When they visit your website, they do leave imprints of the legitimate visit thus polluting your reports. Check in the list that might help you identify spams of either nature.

How to detect referral spam?
The easiest way to detect referral spam in Google Analytics is identifying the unusual and suspicious referrals that don’t have any real reference to your website.
You want to refrain them visiting your site to be sure you can use the data they leave in your reports.
Checking Referral hostname
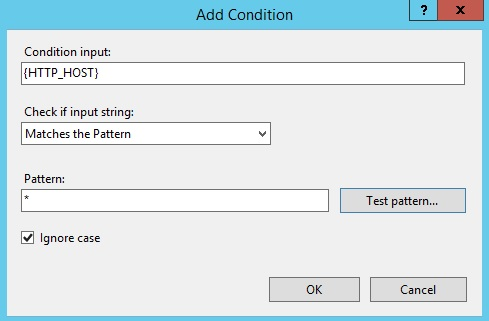
This method is the most reliable method to detect Ghost Referrer Spam, it contains a field either as (not set) or as a fake hostname.To discover the hostname they are using follows the quick steps:
-In the Google Analytics admin window navigates to Reporting Tab.
-Select Acquisition.
-Select All channels by expanding all Traffic.
-Click on Secondary Dimension type Hostname and select.
The Ghost Referrer Spam have an invalid hostnames since they are untargeted whereas the Crawlers Referrer spam, on the other hand, holds a valid hostname.
Alternatives to detect Referral Spam
*Audit the Landing Page
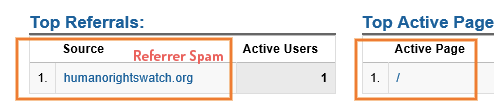
The other way to notice Referrer Spam is by checking the page they are targeting. The targeted page could be either the Home Page (identified by a slash) or a fake page that doesn’t hold any relevance to your website.
* Checking Metric Number
– Spam either accounts for a high or low numbers.
– Navigate to reporting section in your Google Analytics account.
– In the Lateral Bar Select acquisition tab.
– Select Referrals by expanding traffic.
– A table like below will turn up.
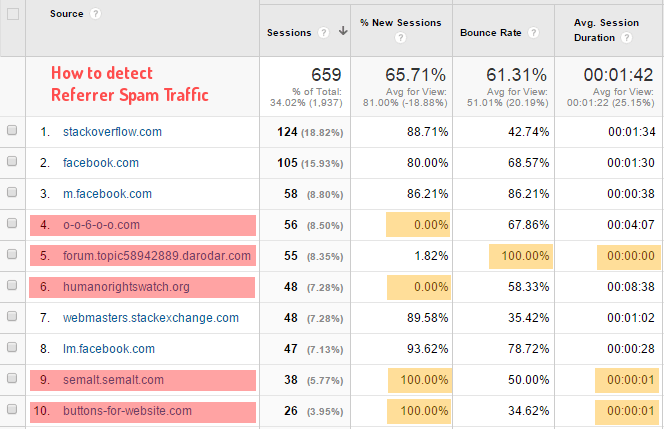
Check with referrals that have numbers like 0% or 100% in new sessions or bounce rate, or average session duration of 0 or 1 Second.
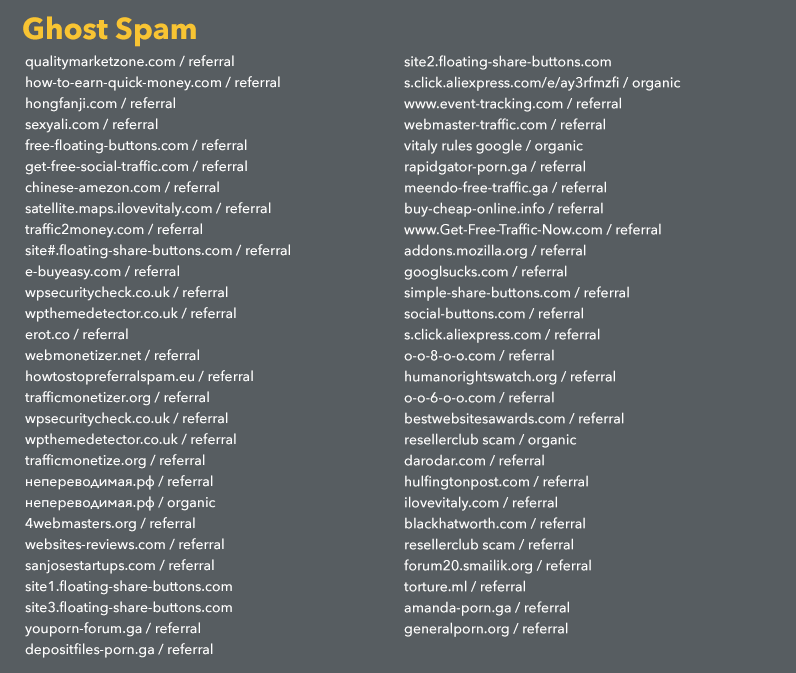
Ghost spam is easier to detect as they use the fake data whereas the crawlers are little cumbersome to analyse. If you still hold the confusion to analyse the referral spam you can access the updated list for the prominent suspected spams.
Stop Referral Spam in Google Analytics
You can go through the valid hostname filters in the Google analytics to stop the Referral Spam creating disasters in Google Analytics report. It will take care of all ghost spam in any form ( Referral, Organic or Fake visit).
If you still find it bit time consuming and still want help in configuring the necessary filters and settings we can give you a hand at [email protected] or call us now at +91 9652744233
Valid Hostname filter is one in a way most efficient filter than the rest of the options available. I haven’t encountered any spam since applying this filter months ago thereby strongly recommend this for use. There are huge advantages of this method over the other.
1. You can stop the spam before it hits you. (Proactive approach)
2. You require only one filter to stop the spam, instead of creating several subsets of filters for the spam as in other options.
3. This Valid Hostname filter will stop ALL the ghost spam in any form whether it shows as a referral, keyword or direct visit.
How Filter Works?
The Most important part of the solution is to work upon the valid hostnames to not exclude any licit traffic.
Note: As a best practice you should always have a view without filter no matter what are the filters for, so if you don’t have one I recommend you to create one.
Creating new filter
Prerequisite is to have a list of your hostnames.
– Visit the Reporting tab in Google Analytics account.
– Within the Lateral tab select the Audience.
– Expand technology and Select Network.
– At the top of the report be sure to select the Hostname because the default you service provider is selected.
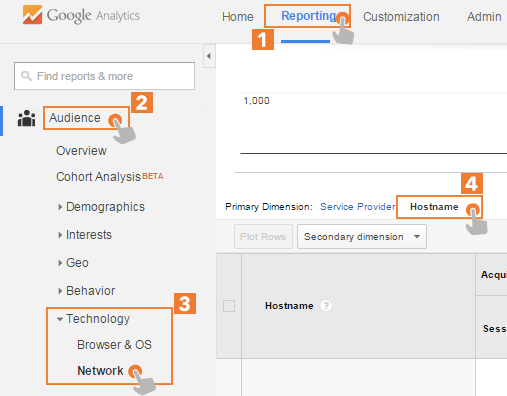 – When you land in there, you will see a table like this and among these find and copy all the Valid Hostname.
– When you land in there, you will see a table like this and among these find and copy all the Valid Hostname.
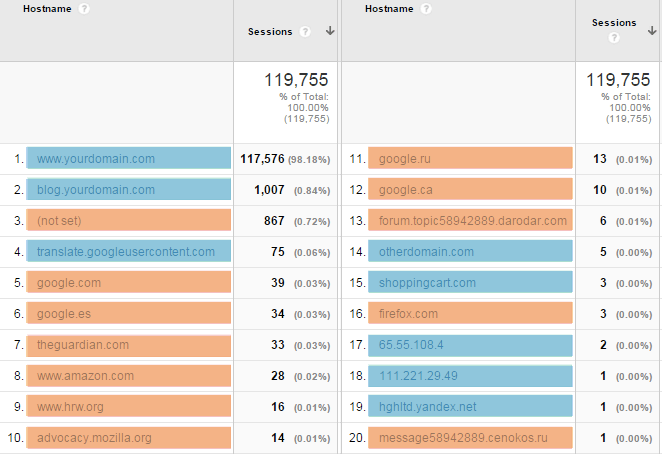
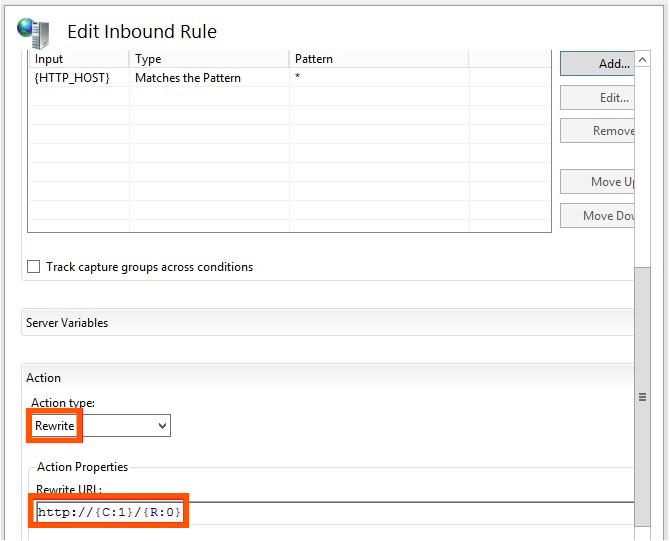
-After gathering the valid hostname, you must create an expression that matches all of them.
yourdomain\.com|otherdomain\.com|translateservice\.com|yourshoppingcart\.com|otherservice\.net
The complexity of expression can range depending on the age and size of the website. If you have subdomains you can omit adding all of them if you are adding yourdomain.com; it will match any subdomain of yours like blog.subdomain.com or support.subdomain.com.
After generating the regular expression, you should add it to an INCLUDE Hostname filter.
– Now in the Admin tab select View where you want to apply the filter.
– Select Filters
Note: If you haven’t created an “Unfiltered” View, create one now it will help you to check later if this or any other filter is working correctly
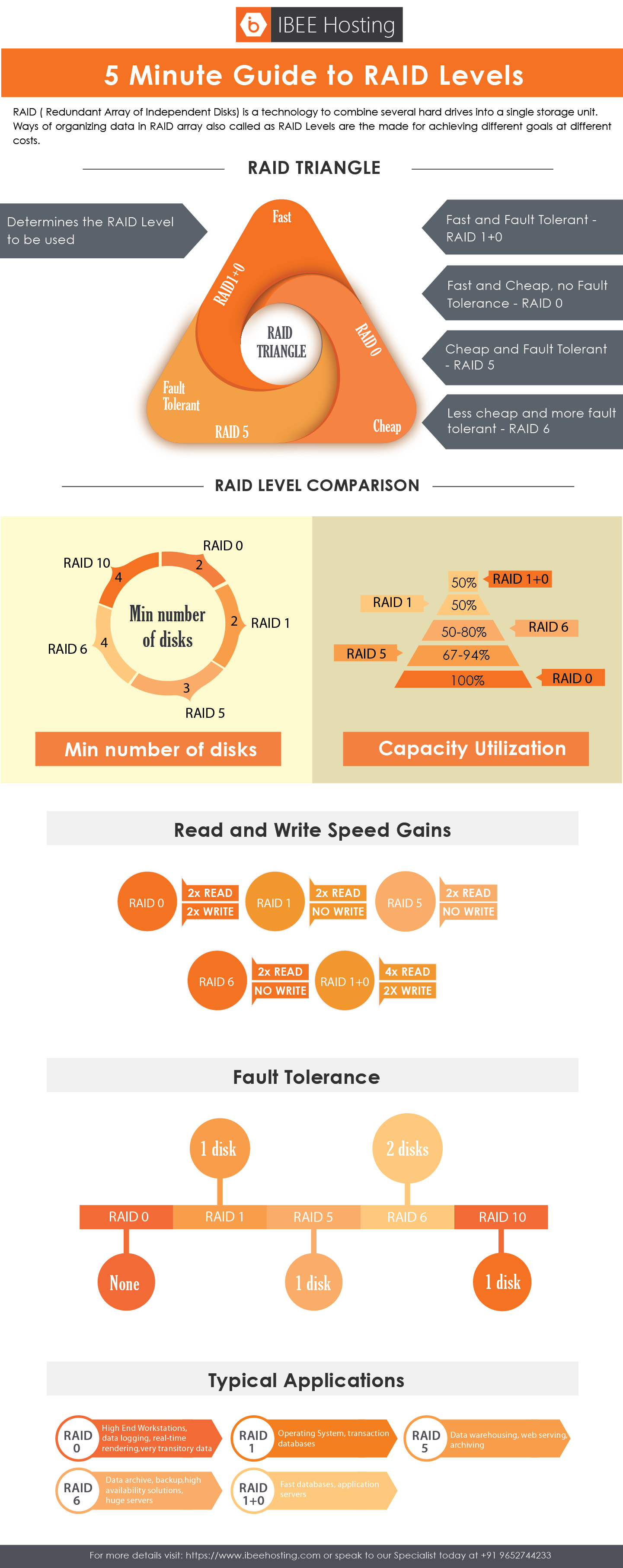
– Select New Filter
– Select Create New Filter and enter the valid hostname filter as a name.
– Within the Filter type choose custom.
– Be cautious you choose include and select Hostname from the dropdown.
– Finally paste the expressions that you built with the valid hostname in Filter Pattern.
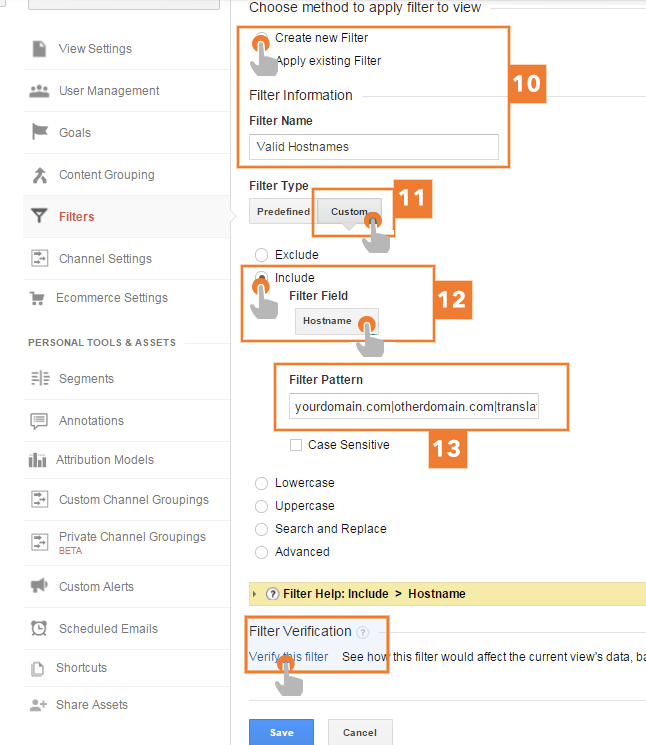
I strongly recommend verifying the filter before application to save time on testings and protecting your data.
Its better to verify data before saving. A table will appear showing you sample data of before and after application of data.
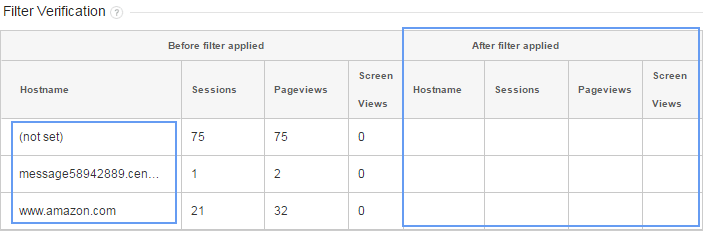
Confirming the data validity, you can proceed to save the filter.
After soliciting the invalid data, you can save the filter. The filter you created doesn’t require much maintenance. It is very important that every time you add a Hostname or include your tracking-ID in any service, you need to include it at the end of the regular expression.
Either it is a webmaster, marketing manager, blogger or a site owner who are investing valuable time and resources cannot afford disrupted statistics altered by spam. Monitoring and continuously optimizing the marketing actions are the main building block of each online strategy; thus the analysis must rely on accurate and reliable data.
Henceforth there is an immense need for the spam free google analytics report.
If you have any doubt about that, contact us now!