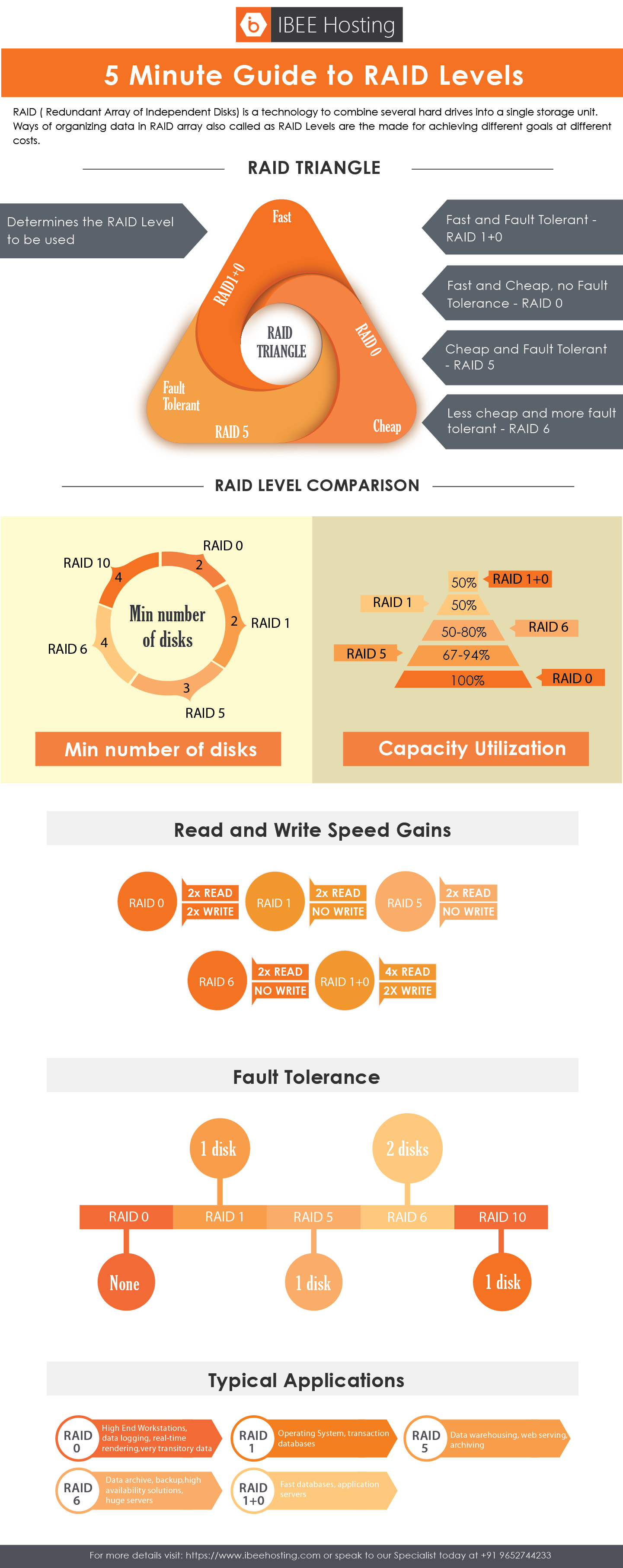
Infographic showing comparisons between the various RAID Levels.
For more details visit: https://www.ibeehosting.com or speak to our Specialist today at +91 9652744233
Infographic showing comparisons between the various RAID Levels.

For more details visit: https://www.ibeehosting.com or speak to our Specialist today at +91 9652744233
As a Google Apps partner we are authorized to send you exclusive Google Apps Promotion codes. You will instantly get a Google Apps Promo Code that works in October 2016. Get 20% discount per user or $10/user off straight away and save money on Google Apps signups and discount varies from country to country. For example, if you need ten users you can save $100 on the payment you make to Google by using our unique coupon codes.
How to apply Google Apps for work promo code and save money?
Once you receive the promo code from us follow below steps to receive the 20% discount (Note – this is for the first time user and the first year of G Suite accounts)
Check the below image for reference and proof that we provide working G Suite(Google Apps for work) promotion codes.
Savings and discounts on Google Apps for work per user vary from country to country:
This Google Apps promotion codes program is currently available only in USA, Canada, UK, Spain, Singapore, Australia, Hong Kong, Brazil, India and few other countries. Others might have to wait until it gets introduced in their respective countries. Also, this G Suite Promo Code program is not available for Google Apps ultimate edition; it is applicable only for Google Apps for Work Edition.
Google Apps is a powerful collaboration suite that comes with a variety of tools like Email, Docs, Spreadsheets, Presentations, hangouts for videos, etc. These tools over the period improved the productivity for many organizations who adopted Google Apps for their organizations IT needs. Several other providers are competing in this space, but Google Apps is a pioneer and the most engineered product I have seen.
Get more work done from anywhere on any device with Google Apps for Work (G Suite). It includes:
Currently there are more than 5 million companies are using Google Apps for Work(G Suite) which was called as Google Apps for business earlier, and we tried exploring other competitive products as well but from my observation Google Apps is the best among the cloud-based collaboration tools. The best part is it works seamlessly across the multiple types of devices and enterprise-class security from Google from its world-class data centres. The latest material design approach gives an edge to these tools to serve content seamlessly across the devices.

Google is more depended on few countries for getting sales like USA, Canada, UK, and Brazil. They get the maximum sales from these countries, and it started invested heavily in digital marketing by giving direct ads in youtube, TVs, and other alternate mediums. We have updated new coupons today, we sometimes offer 50% Google Apps promo codes as well, so hurry up and get benefited with this opportunity.
So far, as a reseller of Google Apps, we have helped more than 200 customers to bring them to Google’s collaborative platform, we help our clients with 24×7 email support for all the migration, setup, and technical queries. Google doesn’t issue any promo codes to any coupons websites like retailmenot, coupons.com, etc. and only works with referral partners and Google Apps resellers like IBEE Hosting.
G Suite Referral Program is now changed to G Suite Referral Program. Selling Google apps or G Suite will get 20% discount to resellers and most of the times customers ask for this discount to sign up with resellers otherwise they don’t see any value in reseller offerings, now discounted G Suite or Google Apps will directly give benefit to customer, This move of Google Apps referral program irked Google Apps for work resellers and started protesting over blogs and forums. This program is a direct competition to Apps resellers where their margins will shrink, and leads will go directly to Google. As a brand, Google always has an advantage against resellers. Though there is a benefit of recurring revenue for partners than one time $15 per user in referral program still Google Apps partners are not satisfied with this kind of approach from Google. Users who joined Google Apps referral program now gets a free domain name for one year from Google Domains.
An early bird’s eye of let’s make the web faster initiative – SPDY (pronounced as “SPeeDY”) came into existence with the goal to mark a substantial decrement in Website Load time. It didn’t imprint the replacement of HTTP but modularised it with the HTTP 1.1 by enumerating no. of features to nimble up web transactions.

SPDY was evolved by Google and soon prospered on almost all the Google Products.In a short span of time, big Tech companies like Facebook, Twitter and WordPress.com soon practiced it.
This article will feature on the basics of SPDY and its functionalities in accelerating your Web Performance.
SPDY Design and features
SPDY adapts itself into the existing architecture by adding a session layer onto an SSL that allows for multiple concurrents, interleaved streams over a Single TCP Connection.
Supported platforms
System Requirements
Before encroaching into the features of SPDY let’s dive deep into the problems that SPDY solves.
Problems that popularised in HTTP 1.1
With HTTP 1.1 number of bugs creeped in affecting the request and response between a client and server. These flaws aggregated to website performance.
Note: Check your website performance, try these online free tools:
webpagetest.org and gtmetrix.com
SPDY is incorporated with the objective of providing functionality that aids in resolving following:
Scarce number of connections
The approach through which HTTP is designed, it says that each resource crave for a separate HTTP request to a server. On an average modern browser supports up to 6 concurrent connections with server. This shows if more than stated connections are required from the same server the browser will have to wait until one among the allocated resources has been downloaded before it can open another request. this phenomenon has significant effect on the page load time.
With the advent of HTTP pipelining this problem was about to elope but it is still penalised with First-In, First-Out (FIFO) problem.
Note: Research accomplished by HTTPArchive shows that the average web page consists of 84 requests from 30 different domains.
HTTP HEADERS
The second issue in HTTP bucket is the use of uncompressed and unnecessary headers.
HTTP headers serves as fundamental to web transactions work but all this has to be directed through wire and so more header you have, the longer request will take.
Today’s technologies that compress the headers are usually optional. There exists still, the potential for compressing or emitting headers that are not required.
Developer workarounds
Web developers have strategically adopted numerous techniques to decrease load times. Few among them are:
Since all these strategies are useful in escalating the load time still, they are very cumbersome to implement.
Troubleshooting these with SPDY
Let us take a look of some of the features that SPDY aims to fix
Multiplexed streams
SPDY accounts for unlimited concurrent streams over a single TCP Connection. Since the requests are interleaved on a single channel the efficiency turns out to be much higher in terms of fewer network connection, fewer but more densely packed , packets are issued.
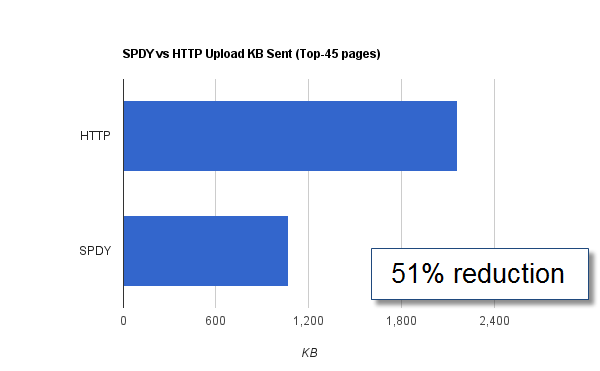
Reducing Download Bytes
Reducing Total Packets
Request Prioritization
SPDY flow include prioritization. Server can be instructed to send the important resources as soon as the available bandwidth is ensured. This helped to overcome First-in First-out problem.
HTTP Header compression
SPDY compresses the request and response HTTP Headers, resulting in fewer packets in transmission with fewer bytes.
Server Push
This a salient feature of SPDY and has an ability to create server-initiated streams. This allow server to push resources down to client prior to client’s request for the same.
This is in command with Data URIs to embed images within the same HTML markup page as We know the required resources to be requested thus eliminating the need for extra request.
Using SPDY Today
Now since you are well versed in SPDY basics and functionalities you can put this into use and reap benefits. The primary gain from SPDY is readily availability primetime. The major notable point is that SPDY requires SSL. This generates a slight latency penalty but ensures a secure connection between the communicating nodes.
Browsers that back up SPDY – Chrome, Opera, and Mozilla Firefox. Microsoft is also among the peers.
Check if a website properly supports the SPDY protocol, the super fast HTTP replacement and troubleshoot any problems with the configuration.- SPDYCheck.org
Disadvantage of SPDY protocol is cPanel doesn’t yet support HSTS and SPDY seamless integration for https only websites. Also some browsers doesn’t have any clue about this and serve the website on both http and https even if you have 301 redirects to one URL on https, this makes duplicated pages and get the website penalised by search engines.
We at IBEE Hosting have experts to configure your Dedicated Hosting Servers with SPDY and HSTS protocols to make your website speedy and at the same time avoid content duplication.
Often Confused with questions like these – when to prefer which flavor of Linux OS? Do these belong to the same family? Are these one versions of the other? Are these up to date? People often dwell on these questions and to choose among the pool in a state of confusion. Here is a quick note that will address all the unanswered questions and can make you understand a basic difference among all.

Fedora
This flavour of operating system is the foundation for the commercial Redhat Linux version. It weighs more on features and functionality along with free software. Fedora can be used freely within a community and has third party repositories this makes it unlicensed distro version of the Linux OS and imparts a community driver feature for accessibility. This category of OS receives a regular update every 6 Months making it a more scalable in terms of performance.
Unlike Ubuntu, Fedora doesn’t make his desktop environment or other software. Fedora project uses “upstream” software facilitating a platform that integrates all the upstream software without adding their custom tools or patching it much. Fedora arrived with the GNOME 3 Desktop Environment by default, even supposing it to be available for other desktop environments also.
Redhat
Red Hat Enterprise commercializes its Linux distribution intended for Servers and workstations. It is the most favored version of Linux OS and relies on open source Fedora version.
This version caters to long releases to ensure stability among its features. This version is trademarked to prohibit the Red Hat Enterprise Linux Software from being redistributed. Nonetheless, the core software is free and open-source.
CentOS
CentOS is a community version of Redhat. It is a community project that takes the Red Hat Enterprise Linux code, removes all Red Hat’s trademarks, and makes it available for free use and distribution.
It is available free, and support comes from the community as opposed to Redhat itself.
Conclusion
If you’re looking for one of the most reliable, secure, and dependable platforms for both the desktop and the server, look no further than one of the many Linux distributions.
With Linux, you can assure your desktops will be free of trouble, your servers up, and your support requests at a minimum.
More Resources:
If you’re looking for more resources to help guide you through your lifetime with Linux, check out the following resources:
Linux.com: Everything you need to know about Linux (news, how-tos, answers, forums, and more )
Linux.org: Everything about the Linux kernel (with plenty of beginners, intermediate, and advanced tutorials)
Howtoforge: Linux tutorials
Linux Documentation Project: Plenty of documentation (some may be out of date)
Linux Knowledge Base and Tutorial: Plenty of tutorials.
After the recent clarification from Google that they treat sub domains as equivalent to new domains web masters having an issue on how to migrate their sub domain blogs like blog.domain–name.com to domain–name.com/blog especially for the large sites having multi server architecture. For example if you have one web server one DB server and log server, if you want your blog to be hosted in log server because of wordpress blog requires PHP and Mysql software in web server and you don’t want to overload your web server with so many software or you want to use WordPress blog from a shared hosting account then you can use this Windows ARR or http proxy, below is the step by step process to configure Windows ARR and http proxy on windows servers.
Internet traffic can be controlled through Application Request Routing which is the prominent feature of the IIS. A proxy server acts as an intermediary router processing requests between clients and or Web server workers on the response side.From the request side a proxy server accepts the requests from one among the multiple clients, and proceed the requests to one of the multiple clients and on the response side, the proxy server accepts a request from the Internet nd distributes it one the multiple web server workers. The Internet assimilates that a proxy server proceeds requests and generate the responses for the same rather than the backend workers.
One among the types of the server is Forward Proxy where Proxy server handles an outbound request from the clients, forward it to the internet and generates the response to the client.
In Reverse Proxy, the Proxy Server handles the requests from the Internet and passes it to backend workers and in return generate the response for the same to the Internet.
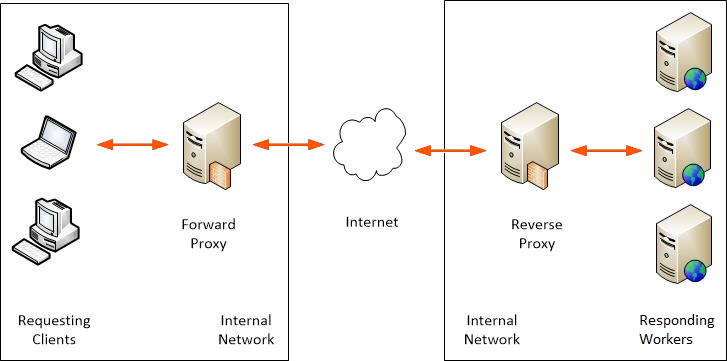
Forward Proxy and Reverse proxy seem to act as a proxy for the request and response side but differ somehow in functionalities. in both the scenarios proxy server isolates the private network from the internet ensuring the security measures applicability.
ARR as a forward Proxy
Serving ARR as a forward proxy, enables ARR to be a part of an internal network( or Intranet) of Clients computer. It can be used to improve bandwidth usage and performance.
Keep a note that ARR Processes only HTTP traffic, none other protocols are being processed.
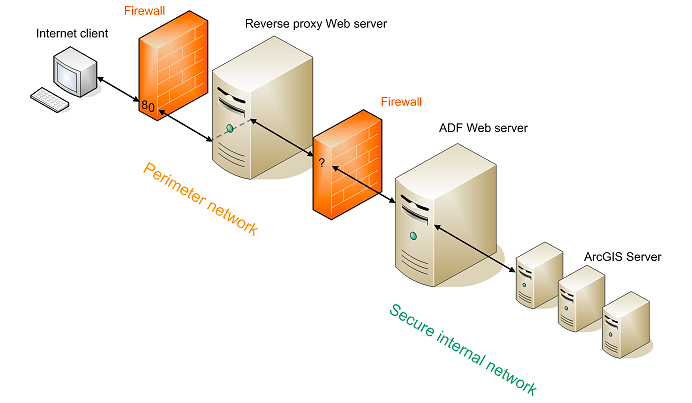
When the clients send the request naming the target web server, it is being processed as follows and forwards it through the firewall to the internet.
Advantages
Installing and configuring ARR as a forward Proxy
PREREQUISITES
To set up a forward Proxy Server following are the obligatory requirements
Configuring ARR as a forward proxy server
To enable ARR as a proxy, and for creating a URL Rewrite rules to enable ARR as a forward proxy, proceed as follows.
4. Go to Server Proxy Setting in the Actions Pane
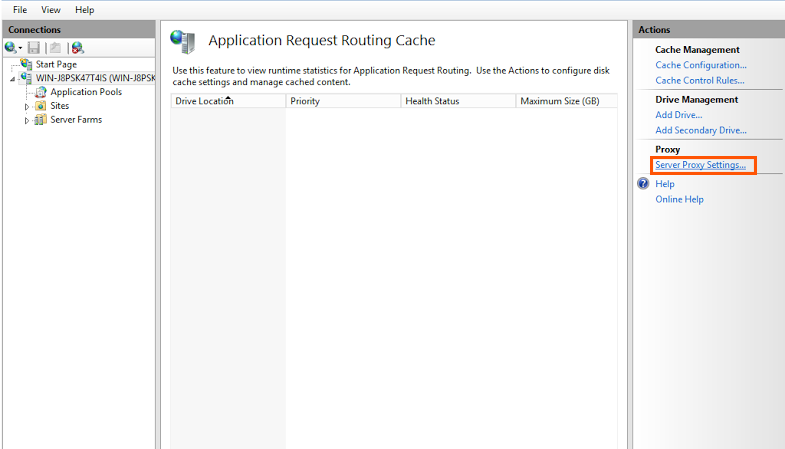
5. In the application Request Routing Page, Select enable proxy
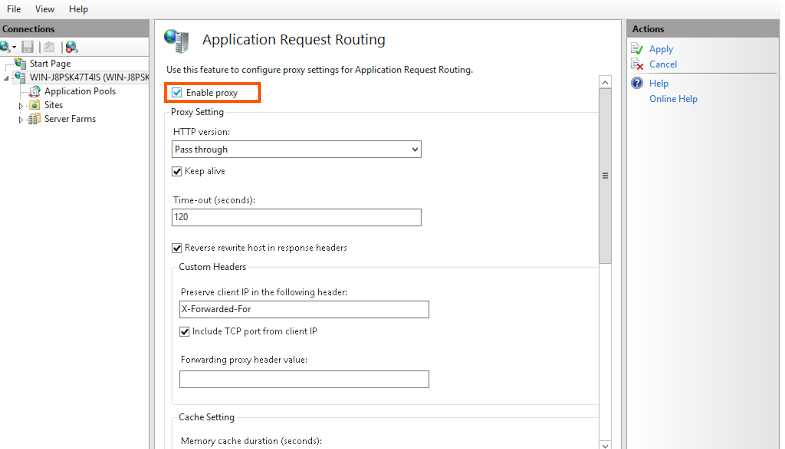
6. In the Actions pane, Click on Apply button. This will enable ARR as a proxy at the Server Level.
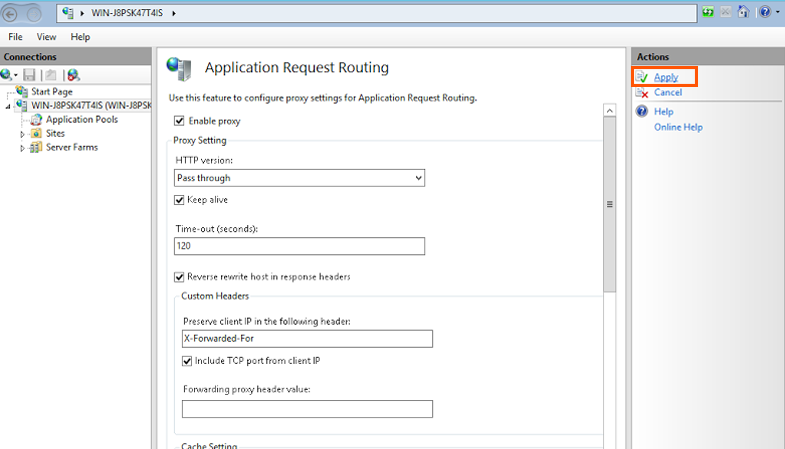
7. To initiate the process of turning ARR into a forward proxy, in the connections pane, Click on the Server node.
8.Double click the URL Rewrite in the server pane.
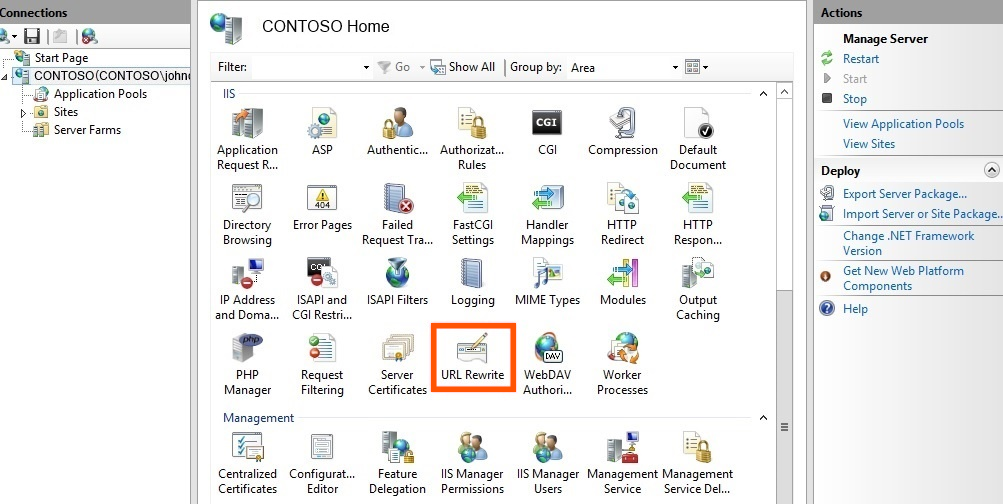
9. In the Actions Pane, Click Add Rule(s).
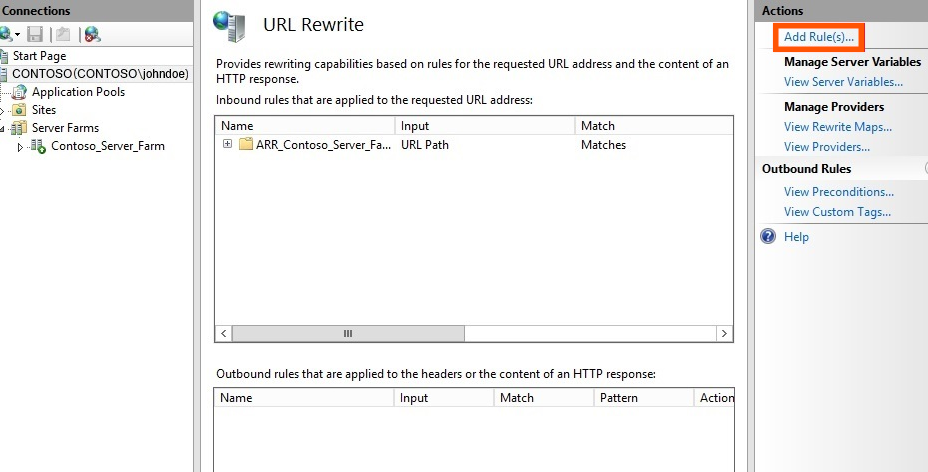
10. In the Add rule dialog box, double- click Blank Rule.
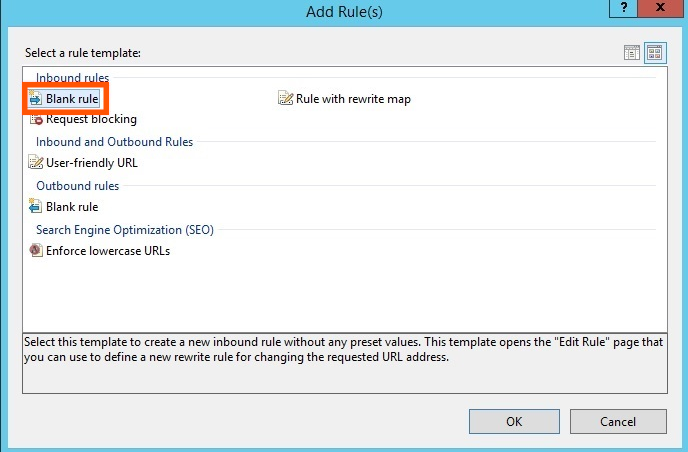
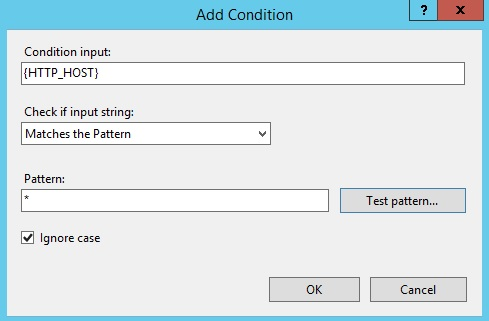
11. Within the Edit Inbound Rule dialog box, enter ” Forward Proxy” for Name. In the Match URL area, enter the following:
Using: Wildcards
Pattern: *
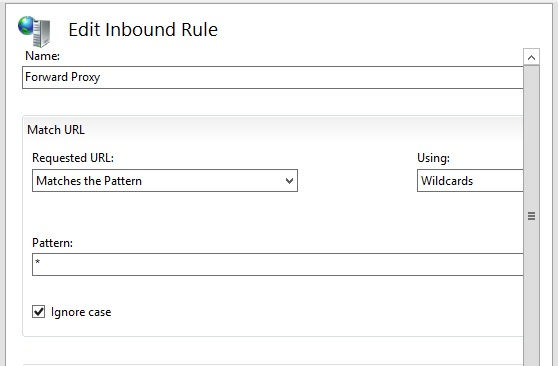
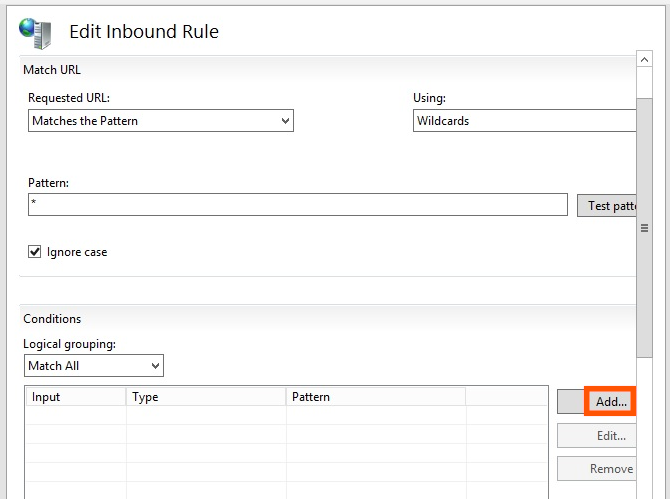
Condition Input: {HTTP_HOST}
Type: Matches the Pattern
Pattern: *
Action Type: Rewrite
Rewrite URL: http://{C:1}/{R:0}
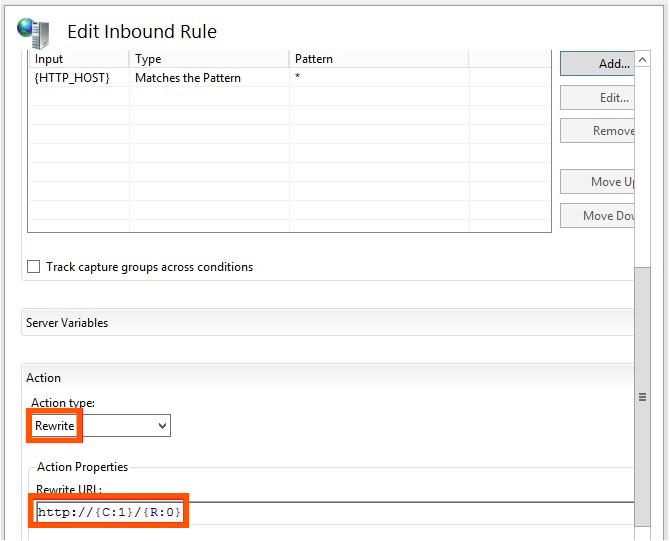
Note: This rule enables HTTP messages to pass through the forward proxy. HTTPS (443) messages are not supported on this forward proxy because ARR does not support HTTP CONNECT.
We introduce our new Business Solutions Email Marketing, Online Surveys and Event Marketing through our Business partner Constant Contact. We offer 60 day free trail, no credit card or billing information required, it is absolutely free to test, additionally we offer free setup and training on how to send emails, generate reports and manage events, we support payment gateways like paypal for event marketing. We also provide time to time promotional campaigns and coupon codes for Constant contact new sign ups and renewals.
Promotion: 40% Off for 3 Months
40% off for 3 months* when you buy Constant Contact before August 30th 2015 and enter the Constant Contact Coupon or Promo Code SP40DISC at here in checkout.
Email Marketing by Constant Contact® is the easy, effective, and highly affordable way to get your message out to your customers, clients, or members. You’ll create high-impact, professional-looking emails—quickly and with no technical expertise. And, most importantly, you’ll build strong connections with your audience that lead to referrals, repeat business and loyalty.
Online Survey by Constant Contact® makes conducting online surveys and polls simple, fast, and highly affordable. No technical or market research skills are needed! You’ll get the insight, new ideas and the knowledge to help meet your customers’ needs. Keep them happy and coming back to do business with you—and grow your organization as a result. You’ll make more informed decisions-with the broader, more insightful view that Online Survey gives you about what your customers and members really think about your products, services, and communications.
Whether a weekend cooking class, a walk-a-thon, or a hands-on workshop, events are an integral part of how you market your small business or nonprofit organization. That’s why you need Event Marketing from Constant Contact. – the simple, professional way to promote and manage successful events. With Event Marketing, you’ll discover the power of online registration.
Click here to get more information and to sign up for a free Constant Contact trail
As with every successful online entity, comes a time when it outgrows its hosting. For most small to medium websites, shared hosting is enough. This type of hosting offers only a portion of a server’s hard drive. All other resources like the processor, RAM and bandwidth are shared among the users. Shared hosting is a cheap starting point until the needs for additional space, computational power and Privacy become unbearable.
At this point, the most popular option to ensure continuous growth is Dedicated Servers. With this service, the user rents the whole server, including all resources. It costs more than shared hosting but allows for a vast array of heavy duty operations as well as increased privacy and security, since there is no one else using the same server.
Dedicated servers come in two types of Account – Unmanaged Dedicated Server and Managed Dedicated Server.
Unmanaged Dedicated Servers, still at a higher price point than shared hosting, are cheaper than Managed Dedicated Hosting. However, all maintenance required is in the hands of the user. Updates, reboots and software integration are the sole responsibility of the customer. Unmanaged hosting is a great, cost-effective solution for people or companies with enough knowledge to keep the server operating at its maximum. When it comes to only one server the savings are not impressive, for the cluster of servers the value increases substantially. Whether it is a dedicated expert, hired on hourly basis, to maintain the server or a team responsible for the whole server infrastructure, unmanaged hosting is only suitable if the entity renting it can ensure proper maintenance.
Managed dedicated servers are more expensive than both shared hosting and unmanaged dedicated servers. The reason is; the hosting company takes care of all necessary supervision and optimization of the servers. They rely on expert personnel to maintain and update the system as well as keeping the machines running at their peaks. Operations like reboots, software installation, updating are automatically done by the hosting company. It is a great solution for people without the required knowledge, time or employees to look after the servers.
Some hosting companies facilitates migration between managed and unmanaged dedicated servers. Whether unmanaged is too much to handle or managed is too costly and unnecessary, there are hosts that would support the transfer one or both ways. This transfer frees the user to leverage further the computational power and security of dedicated servers, as well as enjoy flexibility if the situation requires it. The quality of the bandwidth, servers and support depends largely on the hosting company. Many provide general support for all of their services but at the end of the day, it all comes down to the individual provider.
Dedicated servers are very often a necessary tool for growth. The ability to rent a whole server or several allows websites and applications to operate at a higher level without the limitations of shared hosting. Pricing varies and so do the services, in quality, resources and personnel expertise. Nevertheless, most often than not, dedicated servers are the only way to ensure online growth. The choice between managed and unmanaged is more of a case whether or not the user is prepared to handle server maintenance.
Armed with this knowledge hopefully the confusion and curiosity regarding the Fully Managed and Unmanaged Dedicated Server can be put to a halt. You likely won’t be able to choose your new host in the next ten minutes, but you should at least now know the kind of questions you need to ask. Good luck and let us know if you want to try our Dedicated Hosting services at IBEE Hosting.
Google announced its long pending project “Google Domains” today. As of now this works only for the users who have invitation codes to register or transfer a domain with Google Domains. Google as a registrar from long doesn’t want to get into mainstream domain and hosting business but after the ICANN added several domain extensions off-late Google want to get into this business seriously and applied for extensions like .Google etc and also become a registrar for many top selling and new extensions.

Now we have no idea on how Google Domains want to take into market, is it only website sales or through resellers which are already in the Google Apps ecosystem or using Google Domains referral programs and issuing Google domains promotion codes.
Google Domains features are promising but need lot of clarity like it mentioned here that it provides 100 free email addresses with the domain, so are they Google Apps for business IDs if so what will happen to the current business users who are paying hefty amount and what will happen to the reseller ecosystem. Is there a cap per user number of domains registration and getting email ids? It also mentions about integration with website builders, how Google domains is going to support with website development or building issues is not yet clear.
Security is a crucial aspect of maintaining a Linux Dedicated server and an ongoing challenge for administrators. Especially, as malicious attacks are becoming increasingly smarter and more complex in their nature, posing a constant threat. Although many argue that Linux is inherently safer than other operational systems, it is no exception to these hazards and there are a number of ways to improve security.
Create new user
Upon installation, root is the only user by default on a Linux server. It is advisable to create a new user for server access and usage by the administrator.
Disable root login
The use of root is not recommended unless necessary. Where a superuser is needed, sudo is safer to use than su. Root-level commands via sudo require user authentication and are tracked by default in /var/log/secure. Sudo are specified in /etc/sudoers and can also be edited using the ‘visudo’ utility that opens in VI editor.
Use secure shell (SSH)
Secure Shell is a cryptographic network protocol that offers greater security from password breeches than Telnet and rlogi. Such protocols, using plain text, are susceptible to password discovery via brute-forcing and packet analysis. If an administrator chooses not to use SSH, then particular emphasis should be made on using strong passwords for user accounts and the original root password must be changed.
Although SSH allows the system administrator to communicate with a server using encryption, it is still open to the possibility of an attack. To improve security it is worth removing root entirely as a means of SSH access:
So as to improve password protection, changes can be made to the age-limit of a password or the number of times it is used. For instance, a password may be set to have a lifespan during which it is valid, before expiring:
chage –M 60 –m 7 –w 7
M = Minimum of days required between password changes
m = Maximum days the password is valid
w = The number of days before warning that the password will expire
Alternatively, the use of old passwords can be limited by using PAM module :
The server’s memory will now be restricted to the last 5 passwords used. If a user attempts to enter any of those 5 passwords, an error message will be prompted.
Set-up Firewall
Firewalls are a first line of defense in preventing unwanted data from accessing a server. By monitoring the flow of incoming and outgoing information from the server, a firewall will check a particular flow of traffic against the configuration of a server’s set of rules so as to determine whether to accept or reject it.
To utilize the Linux kernel firewall, IPTables must be enabled. This application allows the system administrator to configure the rules that will be applied by the Linux firewall when filtering incoming and outgoing packets.
The central IPTables files are:
To start, stop and restart IPTables firewall with init:
To start IPTables from system boot:
Update system
Updating the server system is vital. Maintain Linux kernel and running software with the latest available updates to aid in cementing security flaws. To get updates in RedHat or CentOS:
Cleanse system
Software clutter creates greater vulnerabilities and hinders performance. In order to reduce the server’s attack surface and improve its over-all performance, idle and/or unnecessary software can be removed. Packages like NFS, Samba, even X Windows desktop (Gnome or KDE) have susceptibilities and are not needed. Runlevel 3 is the standard runlevel for linux-based servers. To check packages running on runlevel3 use the chkconfig command:
To remove packages:
Netstat network command can also be used to check for any open ports used by programs:
As part of a system cleanse, IPv6 can be disabled if it is not being used. Under network configuration add the following:
Security extension
Use a security extension such as SELinux on RHEL or CentOS when possible. SELinux (Security-Enhanced Linux) is a Manditory Access Control (MAC) provided by Linux kernel. Having MAC enabled, protects the system from malicious applications that may compromise its security. To see if SELinux is running:
Warning display
Having a welcome display that shows a warning when accessing the server is useful to discourage malicious activity. Such a message can be created using Message Of The Day (MOTD). For example, when a user enters the system, a message can appear saying “Welcome . All activity is closely monitored and is being recorded.” To create something along these lines:
Cronjob control
Determining which users can run cronjobs increases control over a system. This can be done using embedded cron files such as /etc/cron.allow and /etc/cron.deny. To permit a user to run cron, add the username to cron.allow and to restrict a user from doing so, add username to cron.deny. Likewise, to permit or deny all, use ALL instead of username. For example, to deny all users from running cron:
Monitor activity
Monitoring user activity and collecting related information is always important, especially when dealing with many users. Logs should be reviewed regularly and it is advisable to move these files to a dedicated log server so as to help prevent intruders from easily modifying them. Common Linux default log files and their usage:
In addition to monitoring user activity and reviewing logs regularly, such information can be stored in order to be revisited for analysis at a later stage if needed. For example, in the instance of a security or performance issue surfacing.
Psacct and acct are useful tools to aid in monitoring activity by running continuously in the system background. They track user activity and the consumption of resources by services such as Apache, MySQL, SSH, FTP and so on. The psacct package is only available for rpm based software such as RHEL, CentOS and Fedora, whereas the acct package is available for software like Ubuntu, Debian and Linux Mint.
To install the psacct package:
To install the acct package:
By default psacct service is disabled and needs to be started manually under RHEL/CentOS/Fedora systems. To activate and run psacct, first check status:
1. # /etc/init.d/psacct status
If status shows message ‘Process accounting is disabled’, then to create a /var/account/pacct file and start services:
2. # chkconfig psacct on
3. # /etc/init.d/psacct start
Once service has started, check status again:
4. # /etc/init.d/psacct status
A message should indicate ‘Process accounting is enabled’.
Recovery measures
Securing a server is not just about protecting it from external threats but also being able to salvage and recover from the impact of a successful attack or any form of system failure.
Backup
Backup important files and keep them safely stored away in a safety vault, at a remote site or even offsite, where they will be available in the event that a disaster recovery is necessary.
Disc partitions
Disc partitions offer greater data security if disaster strikes. By having a number of partitions, data can be both separated and grouped. If one partition becomes compromised or corrupted, the risk of data loss is limited to the affected area. Ensure the following partitions exist:
Third party applications should be installed on an independent file system, under /opt.
Read-only /Boot
Linux kernel and its related files are in /boot directory that is set as read-write by default. Changing it to read-only reduces the risk of unauthorized modification of critical boot files. To do this:
In order to upgrade kernel, these files will need to be reverted to read-write.
Additional measures
In addition to the fundamental ways of securing a Linux server, there are always more measures that can be implemented to ensure the best possible level of security.
Disabling USB ports
Disabling the use of USB ports helps prevent users from attaining valuable data and protects from contamination by compromised USB devices. To ensure that USB detection is not available:
Disable alternative booting
Using BIOS set-up, configure settings to disable booting from CD/DVD, Floppy Drive and External Devices. Furthermore, enabling password protection for BIOS will help restrict physical access to the system.
Disable Control+Add+Delete
For most Linux systems, CTRL+ALT+DLETE is a short cut for initiating system reboot. As a pre-emptive measure, disabling the command removes any chance of accidentally triggering this key combination. To do this:
Final thought
Securing a Linux server is challenging but with the right approach and dedication, exposure to risks can be minimized. From taking security measures against malicious attacks to being prepared for disaster recovery, there are numerous ways to protect a system but ultimately, it comes down to the administrators and how meticulous they are in doing so.


When considering buying a dedicated server, there are some features to have in mind regarding the physical server and of the host providing this service. Choosing the right one depends largely on whether the service package, as a whole, suits particular customer needs. The 10 most important features are:
Operating system
Several different OS are currently being used for hosting purposes. Nevertheless, the two most widely used are Windows and Linux. Microsoft Windows is most suitable for hosting ASP.NET code, MS SQL Server or the use of Microsoft IIS. On the contrary, Linux OS is appropriate for open source stack such as Apache/PHP/MySQL (LAMP) or Ruby On Rails.
Hardware
Hardware, focal of the server can be characterized by its brand and specifications. Branded parts are usually more reliable and have a longer life span. Performance wise, server programs, such as Apache or MySQL, rely heavily on processor speeds and server memory. On top of that, video and audio saturated applications and websites require even higher operating speeds.
As for storage, the two main types in use are SAS and SATA. SAS provides more Input/Output Virtualization capacity while SATA drives offer larger and more cost-effective storage capacities. Applications that are more I/O intensive (e.g. database servers) benefit more from SAS drives.
Bandwidth
Referring to data transfer, together with uplink speed, bandwidth defines the connection between a server and its users. Dedicated servers, being utilized mainly for mission-critical operations and heavily loaded websites and applications, require massive amounts of bandwidth to perform at the desired level. Server hosts make use of high-powered networks through a multi-provider blend of bandwidth, to achieve greater levels of redundancy and a stable 99%-100% uptime.
As for storage, the two main types in use are SAS and SATA. SAS provides more Input/Output Virtualization capacity while SATA drives offer larger and more cost-effective storage capacities. Applications that are more I/O intensive (e.g. database servers) benefit more from SAS drives.
Datacenters
A standardized methodology is used to define datacenters, organizing them in 4 Tiers. They represent the uptime and performance of a datacenter. Tier 3 and 4 offer the best redundancy levels and uptime. Apart from tiers, the location of a datacenter plays a big part in evaluating suitability. Servers housed in a datacenter located in the same region as the customer and the targeted audience are expected to be more efficient than those in a completely different area.
Support
For long term successful business relations, Dedicated server providers have been relying to assist their customers through experts. There are several features that characterize the quality of support. Technical knowledge is arguably the single most important one since customer queries are often regarding software and hardware issues. Response time is also a major factor, having in mind the fast paced environment of the business. Social skills and politeness too, play a big role in customer satisfaction.
Monitoring
Server management relies heavily on resource monitoring and organization. Most Dedicated server providers supply a plethora of instruments that allow timely tracking of data usage and server performance. The tools are often part of an online interface that simplifies the process of monitoring.
Upgrade Options
In line with the increase of performance, storage and bandwidth needs of a customer, most Dedicated server providers allow for hosting plan upgrades. Depending on the initial commitment and particular provider, upgrade paths and pricing can be very efficient. Migrating servers between providers usually is far more expensive than a simple upgrade and a research of the allowed growth is recommended.
Additional services and add-ons
Apart from supplying basic Dedicated servers, providers tend to offer a variety of additional services and add-ons. From hardware, such as firewalls, load balancers & backup, to software ones like recovery and one-click app installation, their functionality and usefulness depend on the needs of a specific customer.
Security
Dedicated servers, being controlled only by the customer, maintain the maximum level of security. Providers utilize extreme measures to guarantee the safety of the data stored on their servers. And often deploy a variety of scanning software specifically targeting invaders, spammers, hackers, and other harmful problems such as Trojans and worms. The leading Dedicated server providers ensure that those software applications that are regularly updating and can combat the newest versions of intrusive elements.
Pricing
The cost of Dedicated servers can vary from high to low depending on the basis of the quality and specifications of the servers, along with the bandwidth and additional services provided. The key target is value-for-money where the customer’s needs are met and exceeded at a fair price.
Choosing a Dedicated server provider is not an easy task. However, considering the major factors that define the service and careful selection should result in a satisfactory outcome. At IBEE Hosting, we will be happy to assist you plan your hardware and service your complex requirements. Write to [email protected] for more details.